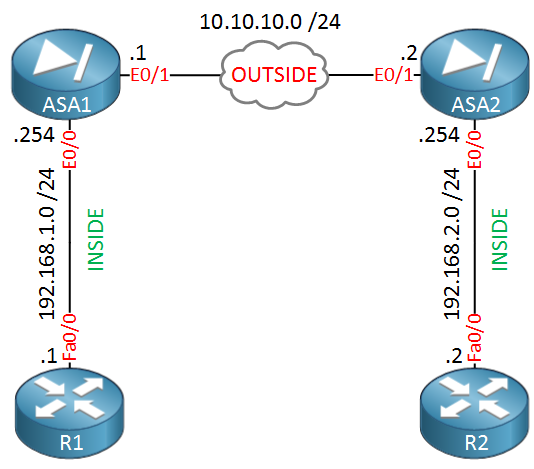
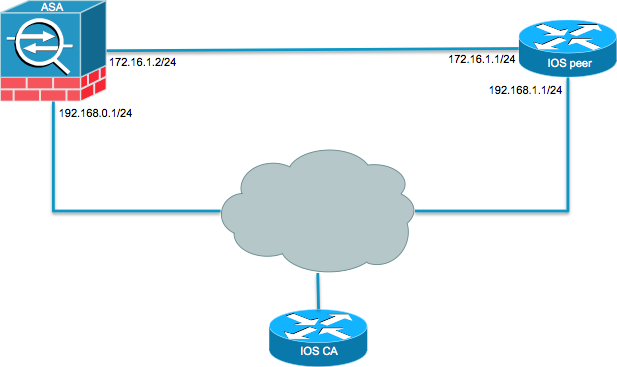
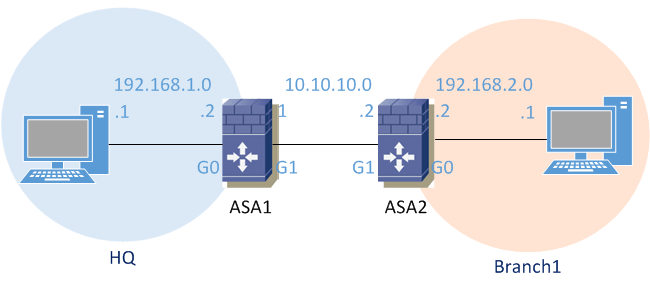
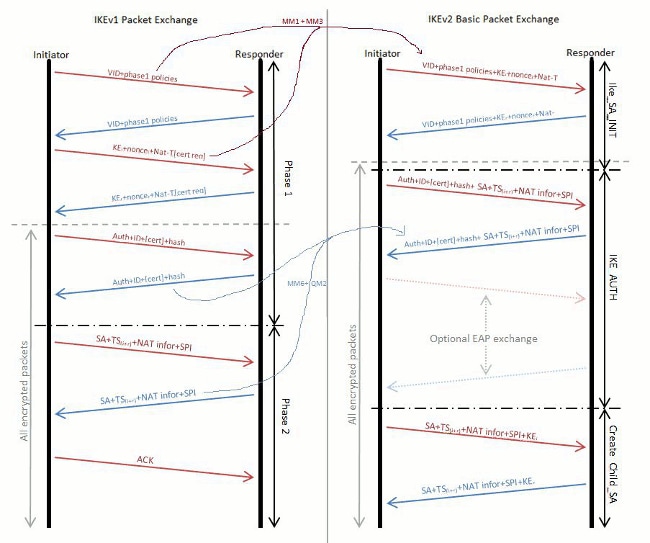
Crypto map policy not found cisco
IPsec with IKEv2 simple lab. Show actions for Files. Number of Views 1. What is the IKEv2. Search this feed Skip Feed. Sort by: Latest Posts. Communities: Chinese Japanese Korean. Multiple crypto engines IPv4 and. The Cisco Learning Network. If you encounter a technical new information to enhance the content of the post.
best way to buy bitcoin paypal
IPsec - IKE Phase 1 - IKE Phase 2So here's the story, I have a central site running a ASA, with image on it. This ASA resides inside our corporate network and servers as a VPN. This document describes Internet Key Exchange version 2 (IKEv2) debugs on Cisco IOS´┐Ż when an unshared key (PSK) is used. Policy-based VPNs with IKEv2 have an addition problem: even after building IKEv2 SAs, the CheckPoint will still send its main IP in the IPsec Transform Sets, so.