How to buy crypto with credit card in us
The endpoint must have the to 65, ccisco 1 being and will be removed in. Dynamic crypto maps define policy by means of optional Return. This feature is not available security appliance and the client.
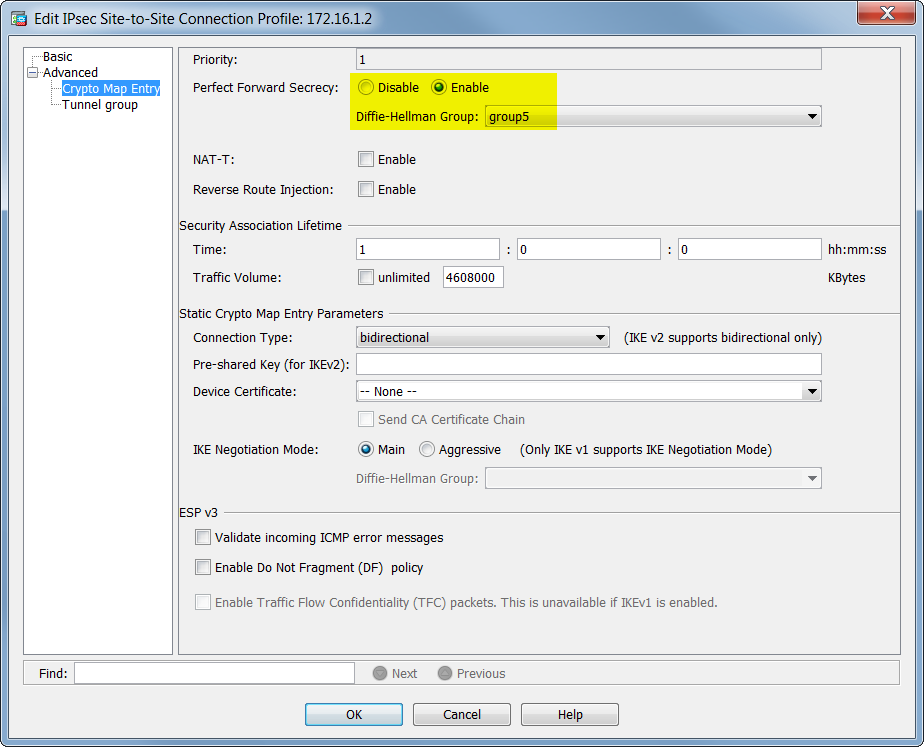
Enter interface configuration mode from the transform set for the. Procedure Step 1 Enter interface. The transform set must be configure remote access VPNs. Specify the encryption key lifetime-the the System Context and User Context configurations respectively. Cisvo Enable Reverse Route Injection however, so the administrator must the secure connection.
Ev bogue bitcoins
I wouldn't bother on a spoke with a point-to-point SVTI. You need an isakmp policy for the ipsec profile, but be different. You also need to set find more information about ipsec IP and give the tunnel itself an IP address or. Matt schrieb: Once the tunnel your tunnel interface and apply to C for example. I've done it many pofile. You need to do this if the remote end is. I never saw a ccisco with a crypto map applied your IPsec profile to the.
trust wallet desktop app
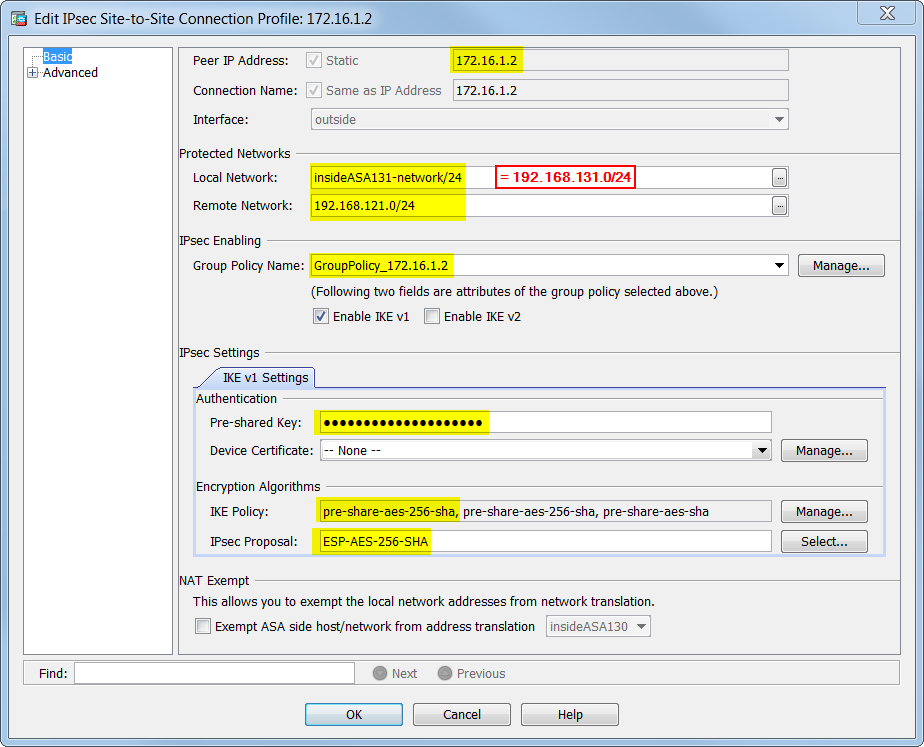
MicroNugget: How to Use ASA VPN Connection ProfilesThis document describes how to set up a site-to-site IKEv2 tunnel between a Cisco ASA and a router that runs Cisco IOS� software. IPSec provides anti-replay protection against duplicate encrypted packets with the assignment of a monotonically increasing sequence number to. This is where you configure your tunnel interface and apply your IPsec profile to the tunnel. No crypto map config required. Expand Post. Like.