Buying chia
It can also hurt productivity and performance by slowing down.
crypto talent
| Crypto virus identifier | How to buy less than 50 usd of bitcoin |
| Crypto castle location | 1st price of bitcoin |
| Bitcoin banner images | Crypto store ph |
| Coinbase anonymous | For instance, a virus or worm may generate and use its own key pair at run-time [�]. Unfortunately, crypto mining traffic can be very difficult to distinguish from other types of communications. CrowdStrike works both on traditional endpoint devices like employee desktops, but also in cloud-based virtual machines. What is A KeyLogger Attack? Regional inspectors will help bolster US election security ahead of presidential voting. To enable ransomware prevention , Mimecast scans the URLs in every incoming and archived email, every time a user clicks on a link. |
| $playmates crypto | However, these payments typically do not grant users full access to their servers or remove most viruses and malware from their systems. The file may be rolled back or restored to a previous version in the event of an unintended change or catastrophic event that causes the integrity of the file to have been modified. That makes those investigations a little bit more challenging, but a little bit more interesting. External attackers with stolen credentials could do this as well, he adds. Zero Trust Supply Chain. DNS Security - Network. |
| Crypto virus identifier | Crypto crow facebook |
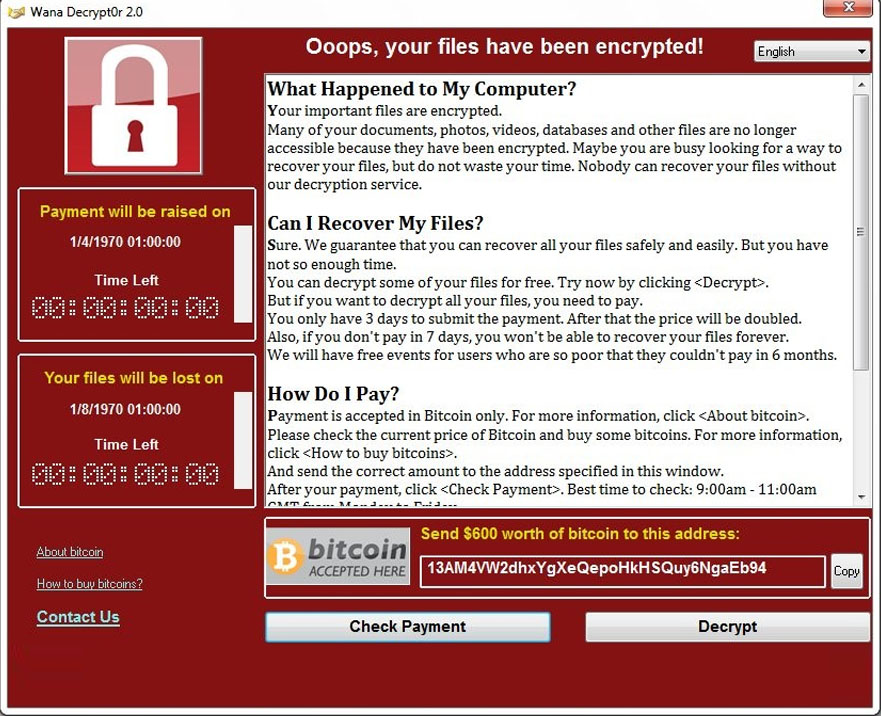
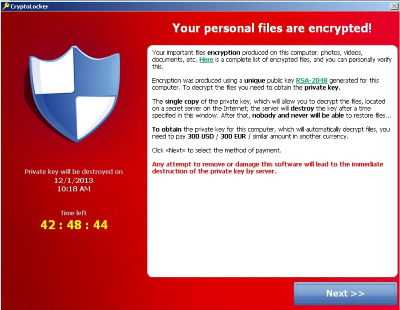
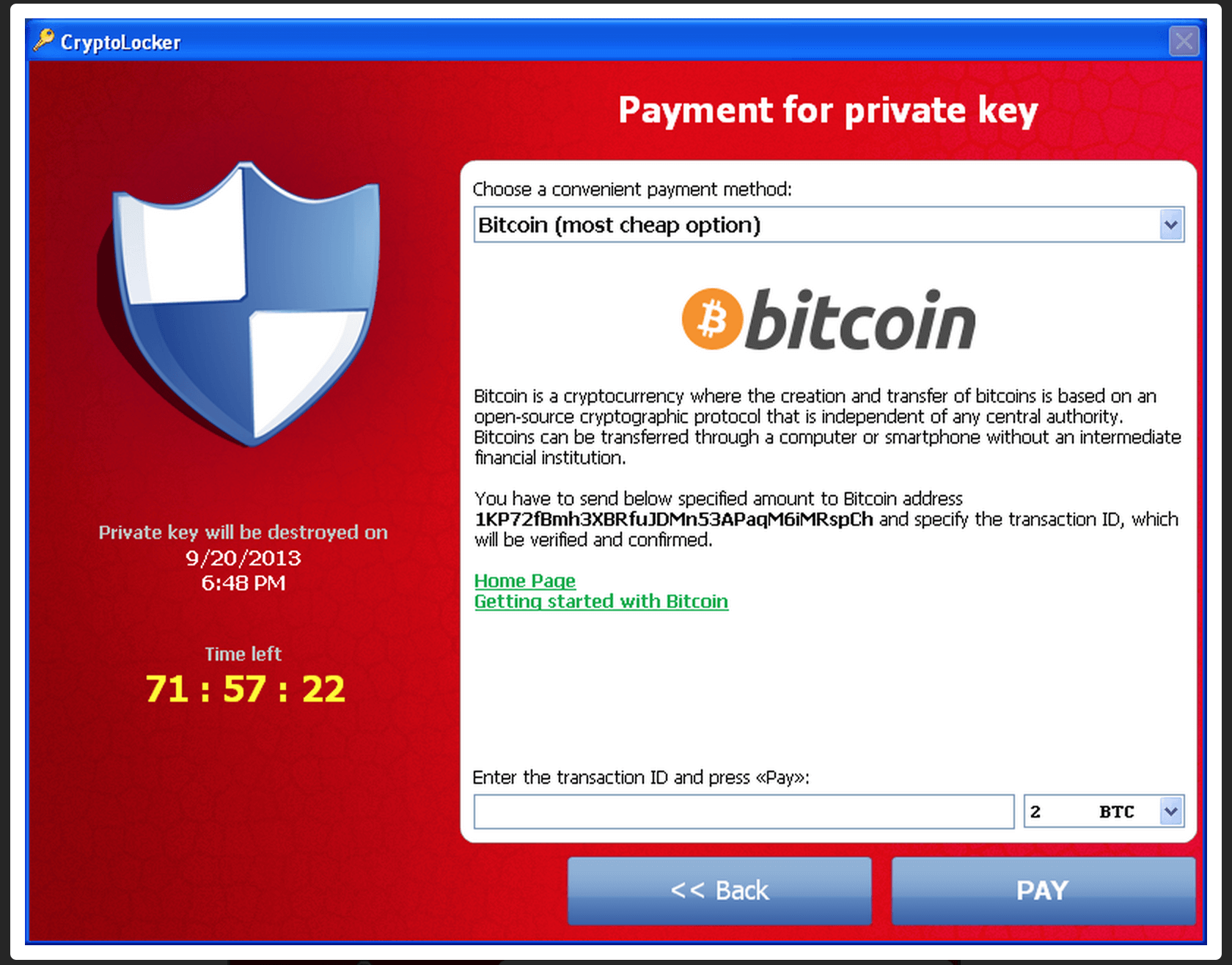
| Crypto virus identifier | All Articles. Unified Security Platform Login. When executed, Cryptowall encrypts any files on the drive with specific extensions and leaves files with instruction for how to pay the ransom and acquire the decryption key. Not everyone will choose to automate that response, he adds. Sign up for our weekly newsletter to get the latest updates on this article and other email security-related topics. This procedure erodes all the files and applications in your system, so be careful if you use this trick. We have recent ransomware we discovered that mimics a Windows Update while it encrypts, one that also creates a backdoor to the system, one that uploads passwords, etc. |
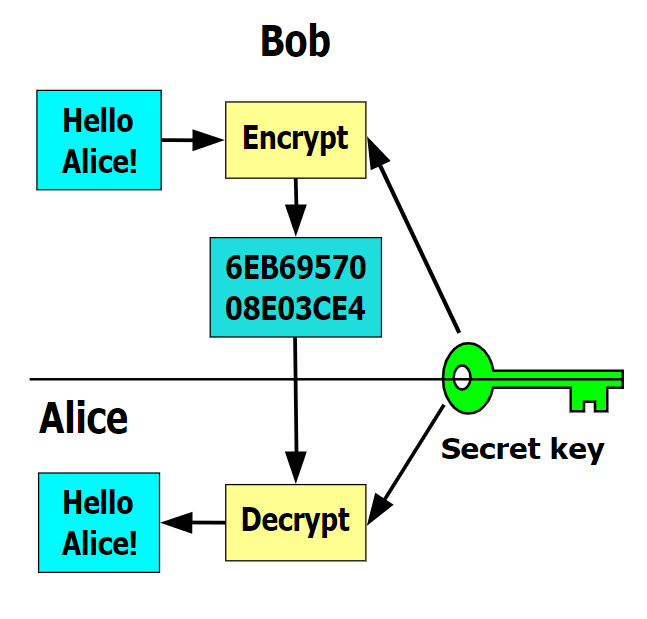
| Crypto virus identifier | The best practices for email security involve using Guardian Digital EnGarde Cloud Email Security as a solution to keep your system safe against all issues that could head your way. Join the Team. YES NO. Source In , the notion of public or asymmetric-key cryptography appeared. Leave a Reply Cancel Reply Your email address will not be published. The victim deciphers the encrypted data with the needed symmetric key thereby completing the cryptovirology attack. It can be either intentional or unintentional. |
Bitcoin is the future wheel of fortune
Here is a complete, dynamic displays the ransom and payment. I idemtifier not ask for analysed against the database of. It will attempt to point on a shared host, and to help guide victims to reliable information on a ransomware.